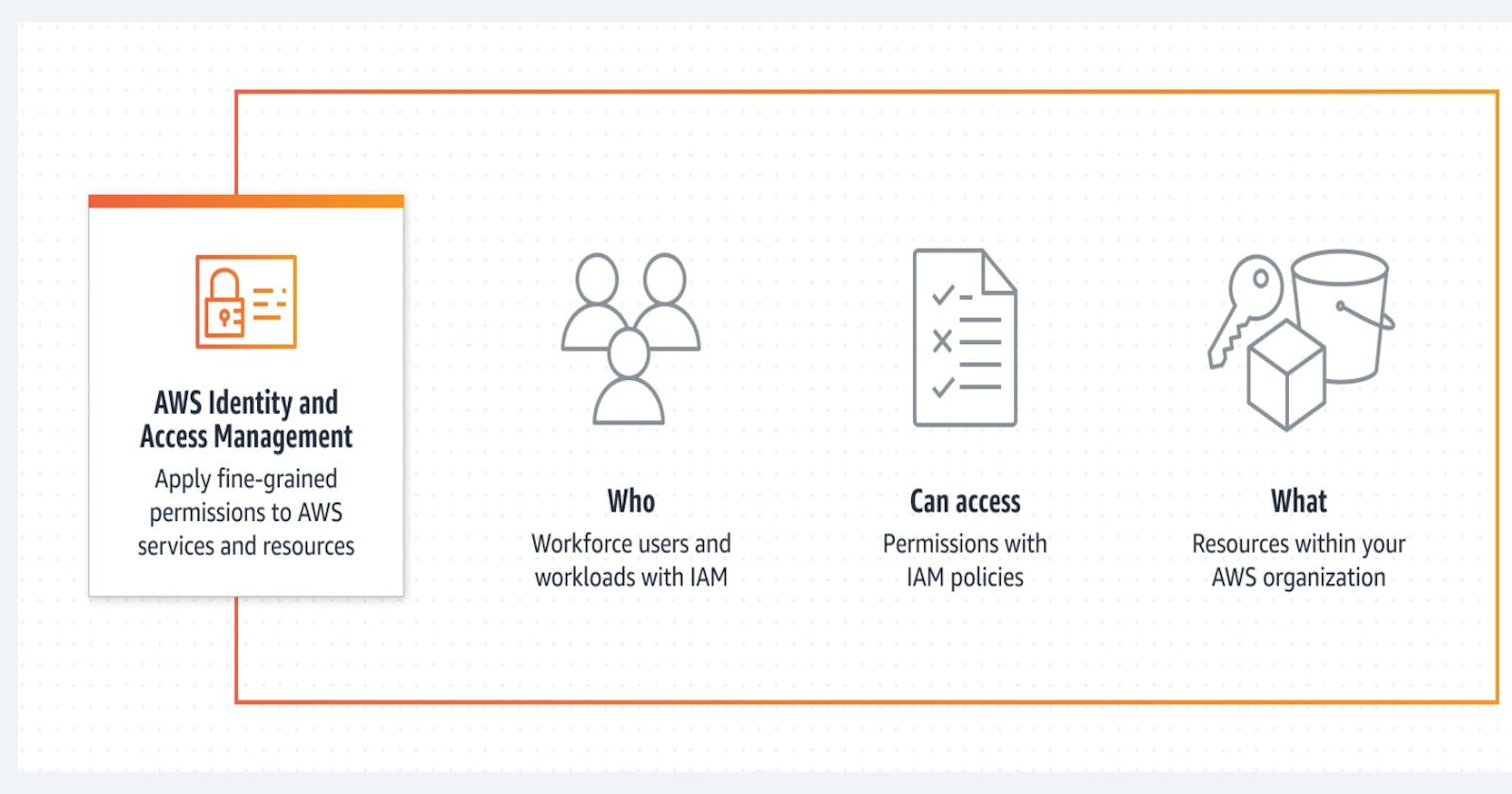
IAM
AWS Identity and Access Management (IAM) is an AWS service that helps you manage access to AWS resources. With IAM, you can create and manage AWS users and groups, and permit them to access AWS resources. IAM is a powerful tool that allows you to control who can access your AWS resources and what actions they can perform on those resources.
Users and Groups
With IAM, you can create and manage AWS users and groups. Users are individual entities that are granted permission to access AWS resources. Groups are collections of users that have common permissions. Instead of assigning permissions to each user, you can assign permissions to a group, which can then be applied to all users in that group. This makes it easier to manage permissions for your AWS resources.
For example, in an organization, we have a development team, an operations team, and so on. We need to give a set of permissions to the development team that is different from those given to the operations team, and then we can use I am here to give a set of permissions to a team.
AWS User
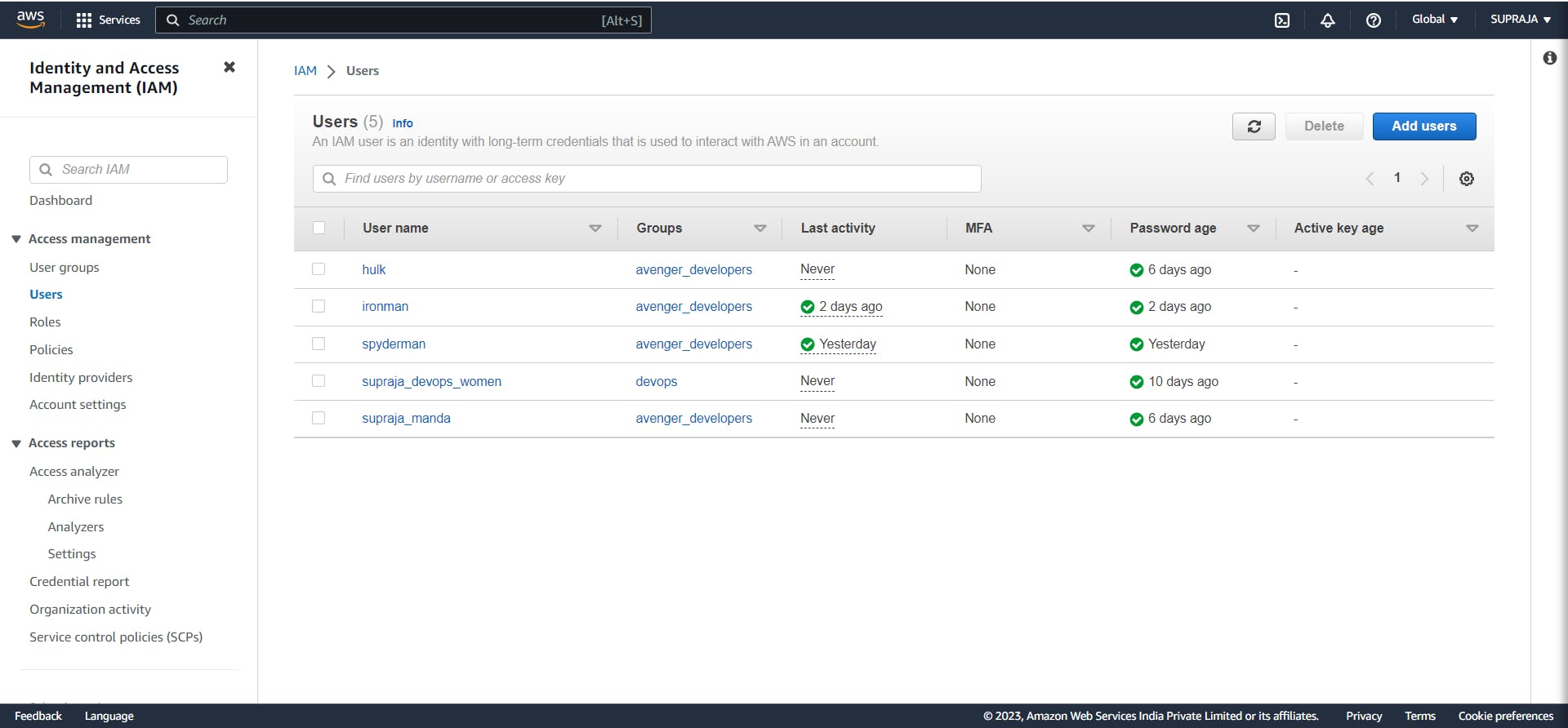
We can add the user using the Add Users button on the top right with a blue color.
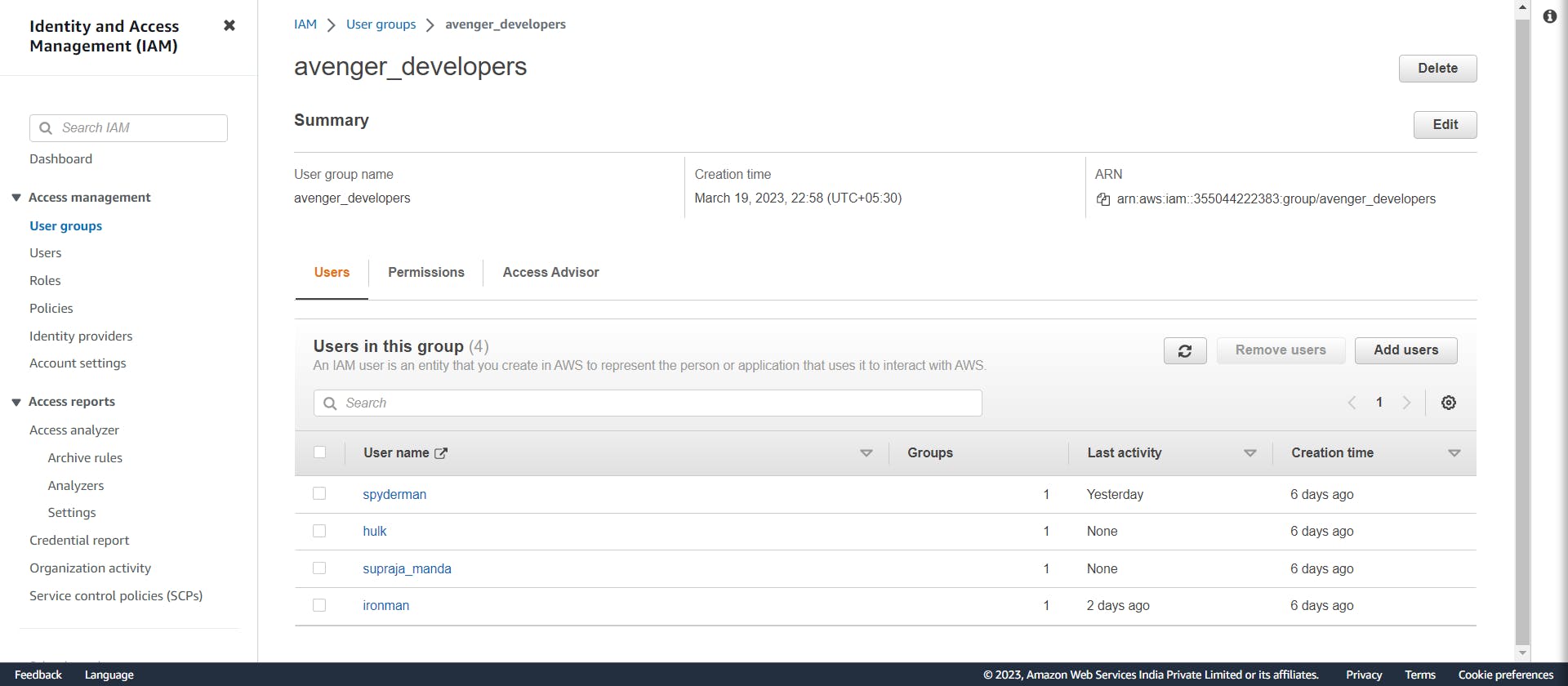
AWS Group
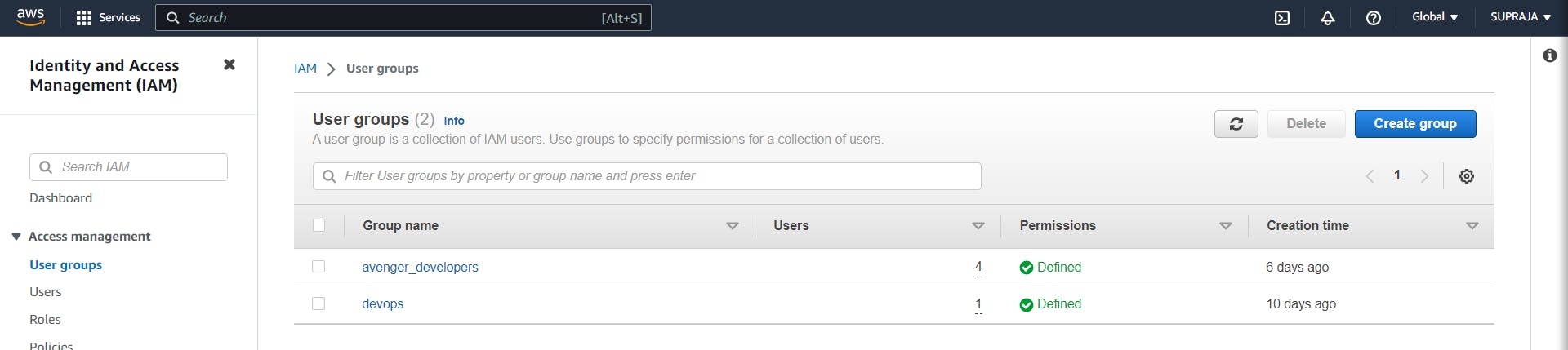
We can create the group using the Create Group button. To add the user to the group, we can click on the group that we want the user to be in. And click on Add Users to add users.
Policies
IAM uses policies to define permissions. A policy is a document that defines the actions that are allowed or denied on AWS resources. Policies can be attached to users, groups, or roles. You can create custom policies or use pre-built policies provided by AWS. IAM policies are written in JSON.
Permissions can be added using Add Permissions. Permissions can be inline permissions or managed permissions.
Managed Permissions.
Managed policies are created and managed independently of the users, groups, or roles to which they are attached. This means that any changes made to a managed policy are automatically applied to all users, groups, or roles that are associated with it.
Inline Permissions.
Inline policies are created and managed as part of the user, group, or role they are attached to, and any changes made to the inline policy are immediately applied to that specific entity
Granting permissions S3 List and Read using JSON for 4 Months
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "S3BucketAccess",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Resource": "arn:aws:s3:::example-bucket",
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2023-03-24T00:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2023-07-24T00:00:00Z"
}
}
}
]
}
Roles
IAM roles are another way to grant permissions to AWS resources. A role is similar to a user, but instead of being associated with a specific person, a role is associated with a service or application. This allows you to grant permissions to a service or application instead of an individual user. You can also use roles to grant cross-account permissions.
Note
IAM is a Gloabal Service
MFA (Multi-Factor Authentication) can be used for more security.
The root user is like God: if we lose the credentials of the root, we are under threat.
We can't create nested groups, which means a group inside another group can't be created.
A single user can be part of different groups.
Conclusion
IAM is a powerful tool that lets you control who can access your AWS resources and what actions they can perform on those resources. With IAM, you can create and manage users and groups, define policies that control access to AWS resources, and use roles to grant permissions to applications and services. If you're new to AWS, IAM is a great service to learn first.

To learn more about IAM, click here.